by George L. Smyth
About five years ago I taught programming and was in charge of the school's AlphaMicro minicomputer. As part of my job I attended a conference where one of the main topics centered around the potential proliferation of a self-replicating program called a virus. The speaker explained how its possible threats, including the alteration of high-level security programs, had been demonstrated on the Pentagon's computer by a person with the lowest level of access. I was alerted to the security needs of my company's computer, but I never thought that this type of problem would filter down to the microcomputer level.
When downloading a program from a bulletin board or merely exchanging disks with a friend, how are you to know if the program is virus-free? Precautions can be taken, such as installing programs that restrict write activities to specified drives, keeping the write-protect window open, and booting the system with a newly formatted disk, but viruses can take shapes that are subtle or delayed, making them difficult to detect.
The first point of assault against computer viruses is to gain knowledge-the ability to recognize the existence of a virus; the second is to gain control-the ability to destroy it. At the vanguard of this attack is George R. Woodside, who has written two programs to help us recognize virus symptoms and remove them.
FLU.PRG is a program that demonstrates the symptoms of several viruses known to exist on programs written for the Atari ST series of computers. These examples include symptoms that attack the sound chip and display, not those that are destructive to the disk. By clicking on one of the selector boxes, the chosen virus symptom is demonstrated. The delayed and/or slow-infesting routines are sped up to make the demonstration more visible. The different examples are:
• Blot: After the system has been on for three hours, the screen is slowly blanked out, one pixel at a time.
• Screen: Similar to the blot virus, this one works more quickly and is invoked after only 30 minutes.
• Green goblin: Every 16th disk access causes a portion of the screen to be flipped upside-down; after 128 accesses the virus's "signature" is displayed.
• Label: Every tenth disk access causes the screen to completely blank out.
• Mad: This category involves eight different attacks, including reverse video, horizontal and vertical scrolling, and scrambling.
• Maulwurf: After a specified period of time, the perpetrator's signature is displayed at the cursor position.
• Mouse inversion: The vertical orientation of the mouse is inverted after a certain number of new disks are detected, i.e., pushing the mouse forward moves the screen pointer down.
• Pirate trap: Possibly installed by a software vendor or developer, this virus copies itself to other disks and every 50th copy displays a message claiming that the user is being watched.
So what can we do about this? How can we know if a newly downloaded program is virus-free? What can we do if it is infected? There are no guarantees, but VKILLER.PRG is able to recognize the current crop of viruses and erase them from the disk.
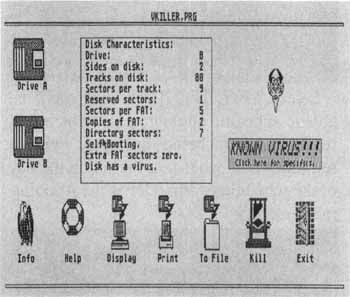
Viruses inhabit the boot sector of a disk. The boot sector allows a program to be automatically executed by resetting the computer or powering it off and then on, a scheme employed by many software developers within copy-protection devices. This type of disk cannot be checked, since VKILLER.PRG searches this boot sector for the presence of any information. There is no way to tell if the information found in an executable boot sector is a virus or represents legitimate instructions. Simply stated, if a program requires a system reset or shutdown in lieu of double-clicking its icon to be run, VKILLER.PRG should not be used to check the disk.
The existence of a virus is searched by selecting the A or B drive icon. The program displays a happy face if the examined disk appears to be clear of viruses. A devil's face appears if the boot sector contains executable code, characteristic of a virus. If the disk does not contain an executable boot sector, but instead contains another form of data where the disk should be blank, a question mark appears. A virus warning box is displayed if the characteristics of a known virus are detected.
If the user detects a possible virus, the "Kill" icon should be selected. This operation erases the unused portions of the boot sector and FATS. Mr. Woodside states that all currently known viruses can be eliminated in this manner. But, as mentioned above, if the disk has a legitimate use for the executable boot sector, the routine will not recognize this and will "Kill" the disk just as if it contained a virus, rendering it inoperable.
The program has the ability to detect the presence of a known virus in the system while the program is running. If this happens, instructions are displayed as to the action which should be taken.
The program displays information about the disk, such as the number of reserved sectors, sectors per FAT, directory sectors and other information.
The user can also send the information contained in the boot sector and FAR, the binary values and their ASCII equivalents, to the screen, disk or printer. This is useful to the knowledgeable individual who wishes to learn more about virus placement on the disk, or to the novice who merely wants to learn more about the software structure of Atari's disk format.
To date, 15 known virus types can be identified by this program. Mr. Woodside urges anyone finding a virus that this program cannot detect to send him a copy so that an update can be implemented. This is an excellent way to support your friendly local public-domain programmer.
