
BY GEORGE WOODSIDE
What They Are, How They Get There and How to Protect Your System
George Woodside takes you on a guide through the cryptic world of computer viruses and shows you how they affect you directly. As a special bonus, we've included his virus-detection program Vkiller on this month's START disk.
An ounce of prevention in VK!LLER.ARC and FLU.ARC on your START disk.
Guilty. With that word, on January 22, 1990, Robert 1. Morris Jr. became the first person to be convicted under a new federal law designed to protect computer systems from malicious break-ins and viruses. Morris was responsible for the "worm" unleashed November 2, 1988, on computers connected via the ARPANET electronic network. Thousands of computer systems locked up as the worm reproduced itself and spread to other computer systems. Indeed, the worm was so prolific that many systems were forced to shut down for days to reload data from scratch just to get rid of it.
Viruses: The Why and the
What
Why programmers like Morris create viruses is a difficult question
to answer. Some want to prove their programming abilities in an age where
"hacking" is the fading art of a bygone era. Others claim that they are
simply exploiting holes in computer security, thus turning a virus into
a good thing. Still others clearly have malicious intent. In the end, no
matter what theory you subscribe to, one thing is clear: a computer virus
is no fun, especially if you're the victim.
So, what exactly is a computer virus? There are plenty of buzzwords circulating through the industry and there is some disagreement on precise definition. Generally speaking, a computer virus is a concealed program that imbeds itself into another program to be spread and eventually executed. However, the Morris virus has been characterized as a worm because it did not imbed itself into anything. Instead, it sent reproductions of itself from system to system via an electronic network. Another common virus, known as the "Trojan Horse," is a seemingly useful program that conceals another, secret, program or function.
In the ST world, worms are unheard of because there are no significant networks through which they can spread. Neither are there any known Trojan Horse programs in the United States, at least not yet. A particularly nasty Trojan Horse was recently distributed to MS-DOS system users in Europe. It moved all the files on the user's hard disk into hidden folders, then encrypted their names. The victims were instructed to pay the perpetrator a "license fee" of over $300 for software to recover their files. Fortunately, no one did: a recovery technique was quickly developed and distributed by virus fighters.
A number of viruses have, however, found their way to the ST in both Europe and the United States.
Viruses on the ST: Two
Flavors
Viruses on the ST manifest themselves in two ways: boot sector and
link. A boot-sector virus inserts itself into the very first (boot) sector
of a floppy disk. It resides only on that disk, until the ST is powered
on or reset with an infected disk in Drive A. When that happens, the virus
loads itself into memory and becomes part of the ST's operating system.
The boot-sector virus' mission is twofold: to spread itself to more disks and to eventually launch some kind of attack. This is the easier type of virus to create and detect, and so far all boot-sector viruses reside on floppy disks - none are known to infect hard disks. Doing so would be futile anyway, since the virus depends upon removeable media to spread and hard-disk drives remain within a single system. Of course, with the introduction of removeable hard drives, all that could change.
Link viruses are more sophisticated. They do not attack the boot sector of a disk, hut modify programs directly, imbedding (i.e., "linking") themselves into a program's executable code. The modified program then installs the virus into the ST's operating system each time that program is run. Once installed, the link virus spreads into any other executable code it finds and eventually launches its attack.
While they are reportedly spreading in Europe, I am unaware of any link-virus attacks in the United States as of this writing, though it is just a matter of time before they are as widespread here as in Europe.
How Viruses Spread
When talking to the victim of a virus, there are two statements I always
hear: "I never thought it would happen to me" and "How did this happen?"
Well, nobody ever thinks it will happen to them, but it does, every day.
If you don't make regular backups of hard disks and keep backup copies
of important floppy disks, the results can be disasterous.
| FLU |
 Familiarity with the way a known virus attacks your system is helpful in recognizing when one is present. To that end, you'll find Flu indispensable. It's a collection of the effects of some of the viruses found on the ST. Flu is a demonstration program only - it does not contain any of the virus code. It does contain the nondestructive "attack code" of several viruses. These attacks are either audio or visual, so there is physical evidence of an attack as it occurs. Note: there are no simulations of any of the virus attacks that cause damage to disk data, since there is no way to recognize when such an attack occurs. To run Flu, copy FLU.ARC and ARCX.TTP onto a blank, formatted disk and un-ARC FLU.ARC by following the Disk Instructions elsewhere in this issue. Make sure FLU.PRG and FLU.RSC are in the same folder. At the Desktop, double-click on FLU.PRG. Flu runs in all three resolutions; documentation is included in FLU.TXT. |
Where a virus originates is almost anyone's guess but once released, it can spread like lightning in a number of ways: through user-group disks, BBSs, even commercial software. Late last year three companies - Sub-Logik, Strategic Simulations (SSI) and Neocept - inadvertantly released viruses on early versions of PageStream, Star Command and WordUp respectively. In each case the virus was detected soon enough for each company to rectify the situation before it got out of hand.
Once you have an infected disk, how does a virus get into your ST? When a computer is booted up from a power-off state or reset (in most cases), it executes code from its internal ROM (Read-Only Memory). The ROM sets up primary vectors, minimal system configuration information and performs some fundamental tests to find out what devices are attached and get them into operating status. It also checks the boot sector on an inserted floppy disk for executable status. If that's the case, the code contained in the hoot sector is executed. That code may load data files, execute programs, set variables or vectors, add new device drivers - nearly anything imaginable, including infecting the system with a virus, if that's what the hoot-sector code contains.
Now that the virus has managed to get onto a disk and get booted into your system, it must accomplish two things. The first task is to spread itself. Normally it will write itself onto nearly every disk that passes through the ST while the virus is active. Some are smart enough not to write themselves onto disks that already contain executable boot sectors. Any disk with an executable boot probably requires that boot-sector function to be useful. If the virus destroyed the boot sector by writing itself on it, the user would notice it, because the software on the disk would no longer work. That may lead to discovery of the virus before it has the opportunity to accomplish whatever task it is designed to do.
Many viruses run what are known as "counters." Some count the number
of already infected disks they have seen, some count the number of disks
they infect, while others simply count the number of disks that the machine
accesses. In any case, the counting viruses have some threshold they're
trying to reach. When they reach that number, they (presumably) consider
themselves thoroughly spread and assume it is now time to start their attack.
| VKILLER |
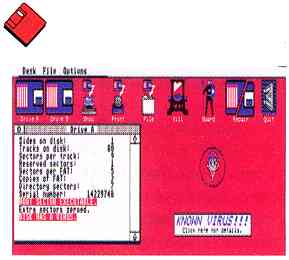 Check every disk, each one with a virus must be cleaned. The ST has fallen victim to a number of known viruses. The public-domain program Vkiller will not only detect a virus on any of your floppy disks, it will also erase the virus if it finds one. To run Vkiller. copy VKILLER.ARC and ARCX.TTP onto a blank, formatted disk and un-ARC VKILLER.ARC by following the Disk Instructions elsewhere in this issue. Make sure VKILLER.PRG and VKILLER.RSC are in the same folder. At the Desktop, double-click on VKILLER.PRG. Vkiller runs in medium and high resolution; documentation is included in VKILLER.TXT. If you do find a virus, kill it, then reboot your system with that disk. Once your system is up and running without the virus, check every disk you own. Each disk that has the virus must be cleaned. Note: Vkiller will eradicate boot-sector viruses without altering any files or programs on the disk. You cannot, however, disinfect any disk that must have its own executable hoot sector. (Any disk with its own executable boot sector will always instruct you to insert the disk in Drive A and reset or turn off-then-on your computer.) Performing a kill destroys the executable boot sector. If you do come across an infected disk that has an executable boot sector, have it replaced with a clean one. |
What a Virus Can Do
Once in your ST, what exactly will a virus do? Almost anything, really
-the limits are imagination and code space. The most harmless virus I've
seen actually purports to be an antivirus. It blinks the screen on boot-up.
The idea is that if you see the screen blink, you know that this harmless
virus is on the disk, rather than a more malicious one. It does, however,
spread itself just like any other virus.
Several viruses attempt to simulate hardware problems. (Conversly, I've had several pleas for help with a suspected virus that actually proved to be a hardware malfunction.) Frequently these viruses use timers to delay their actions until the system has been running for some time and to spread out their activities to make the problem appear intermittent. Such virus-induced glitches include the occasional faked successful disk I/O, while actually not performing the read or write; altering the data being read or written; and, more commonly, screen-display glitches. It is very difficult for anyone to determine whether such incidents are the result of a virus or an actual hardware problem. When such incidents occur on your system, it's wise to execute whatever virus-detection software you have before lugging your system to have it serviced.

Convicted worm creator
Robert T. Morris Jr. faces up to
five years in prison
and a $250,000 fine for violating the
1986 federal computer
abuse and fraud act.
Protecting Your System
Be aware that computer viruses are circulating and can turn up on nearly
any disk you receive from an outside source. As I mentioned, viruses have
accidently been distributed on commercial games, word processors and on
sample disks enclosed with software books.
The simplest and most effective way to protect yourself is to apply write protection to whatever disk you receive before you insert it into your ST - be they from the public domain, a user-group, a commercial source, wherever. Next, make a backup copy, if possible, then run the disk through a virus-check utility. (Editor's Note: As a matter of policy, START'S programs editor runs every submission disk through Vkiller. She often finds viruses.)
Another very sound defense (especially for hard-disk systems) is what I call the "clean boot disk." Format a disk, write protect it, then check it with a virus detector. From now on always boot up your system with that disk. Try to keep it in Drive A as much as possible, so that any time you reset the system, your clean boot disk is present in the drive.
Finally, back up everything. Hard disks, floppy disks, tapes, whatever. Make backup copies, write protect them and store them in a safe place away from your system. If you're attacked by a destructive virus, your first problem is to rid your system of the virus. Do not go to your backups until you have determined if your problem came from a virus, and if so, that you have removed it from the system. A backup is useless if you give a virus a chance to attack it as well as your working copy.
Despite all the precautions, you still may become the victim of a virus. How do you recognize when an attack occurs? It's not always as simple, or as straightforward, as it seems - what may appear to be a hardware problem may be a virus and vice-versa.
a virus is the easiest to detect.
There is no absolute way to determine if a given symptom is caused by a program error, a hardware error, a virus or something else. When files vanish or become unreadable, it may be due to any of several reasons. Poor media or abuse of media is not uncommon. A dirty disk-drive head or one that drifts out of alignment can cause previously reliable disks to produce errors. On the ST, there's the age-old problem of chip sockets having poor contact and early versions had some component reliability problems that could contribute to disk errors. Another, more frequent cause is the use of extended capacity disk formats, some of which are not entirely reliable.
Play It Safe
Fortunately, of all the potential problems to your system, a virus
is the easiest to detect. Use your virus-detect program and start searching.
If you can't locate a virus, then your problem could be any from the list
above. If you do find a virus, be sure to take every step available to
insure that the virus has been eradicated before accessing your backups.
George Woodside is well known for his fight against viruses on the ST. He lives in Woodland Hills, Calif.; this is his first article for START.